Attacking Active Directory
Active Directory Theory
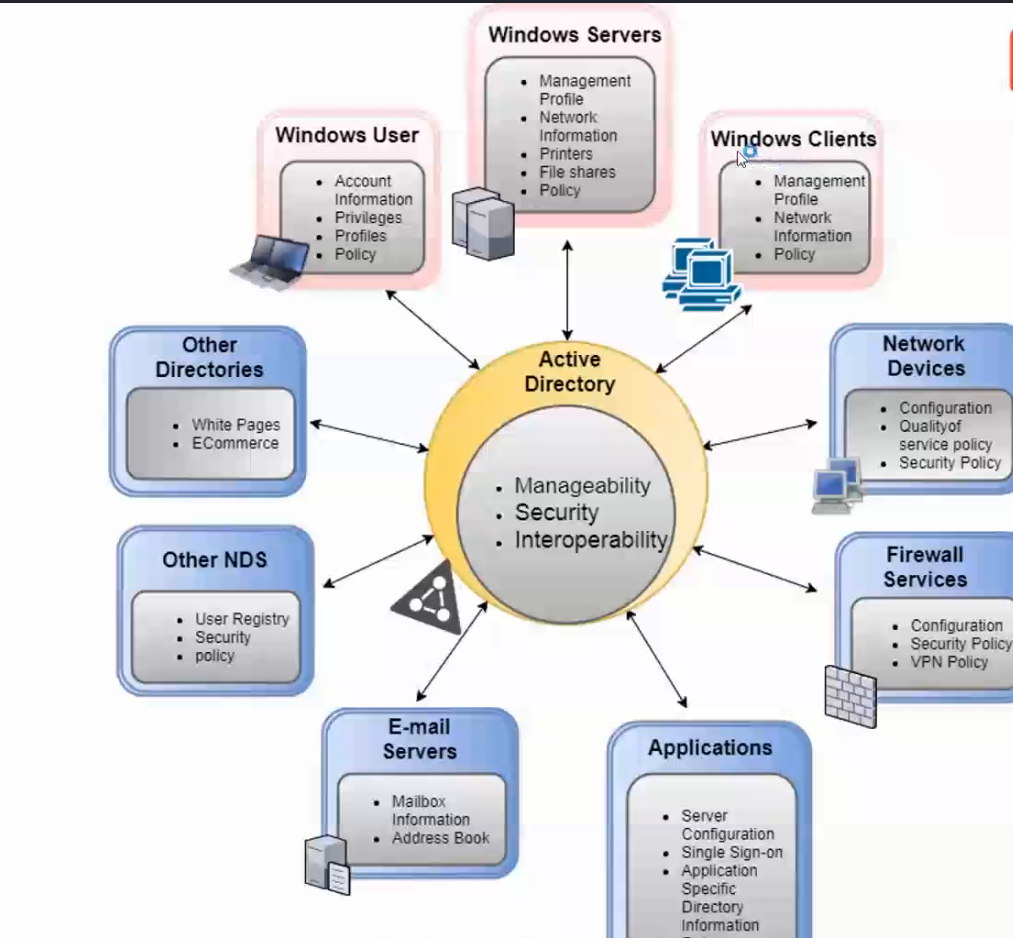
Acitve directory is used by most of business and corporations. You launch a corporation product.com this is called forest. There is DC(Domain Controller) for this forest which holds User Accounts and Computer Accounts. There are multiple departments/subdomains inside this forest like Marketing department, Accounting department, Finance department, Sales department, IT department, etc. These are in heirarchy like marketing.product.com, sales.product.com, accounting.product.com, IT.product.com, etc. Each subdomain have their own domain controller. In the forest product.com the user objects are containarized as groups like Domain Admins, Workstation Admins, Users, IT Group, Support Group, etc wheares the computer objects are containarized as organizational units like Workstations, Servers, Database Servers, Fax, Printers, etc. We create group policies eg: marketing group cannnot access resource of Finance Group but IT group can access resource of Sales group like this. Now suppose you launch another product named boom where root domain will be boom.com this domain may have its own child domains sales.boom.com, marketing.boom.com, etc since you launched boom.com you will configure boom.com to share the same layout or schema(database layout) as product.com. Now, according to configured trusts boom.com will have permissions to access resources of sales.product.com and so on but vice versa may not be allowed, IT.product.com and marketing.boom.com may be allowed to access each other's resources due to bi directional trust setup, etc. Every DC has copy of AD database and when changes is made to the schema this change is replicated to every single domain in the forest. Every single domain eg: sales.product.com, marketing.product.com has its own DC(Domain controller).Everything like computers,printers,fax,servers, etc are called objects in AD. Now how will one user of boom.com be able to find suppose a printer in sales.product.com? In AD there is a server known as Global Catalgoue Server or GC which is like a index page in dictionary which tells where each individual objects are but not detailed description of objects.
Attacking Active Directory
Kerberos Introduction
There are two main authentication protocals for active directory they are NTLM and kerberose.Kerberose is the main authentication protocal.It uses tickets to authenticate.It is considered secured becaus it avoids storing passwords locally and involves a trusted third party(KDC) and has a built in symmetric cryptography.

Authenication server: It confirms that a known user is making an acess request and issues a TGT(Ticket Granting Ticket)
Ticket Granting Server: It confirms that the user is making access request to a known service and issues a Service Tickets(ST)
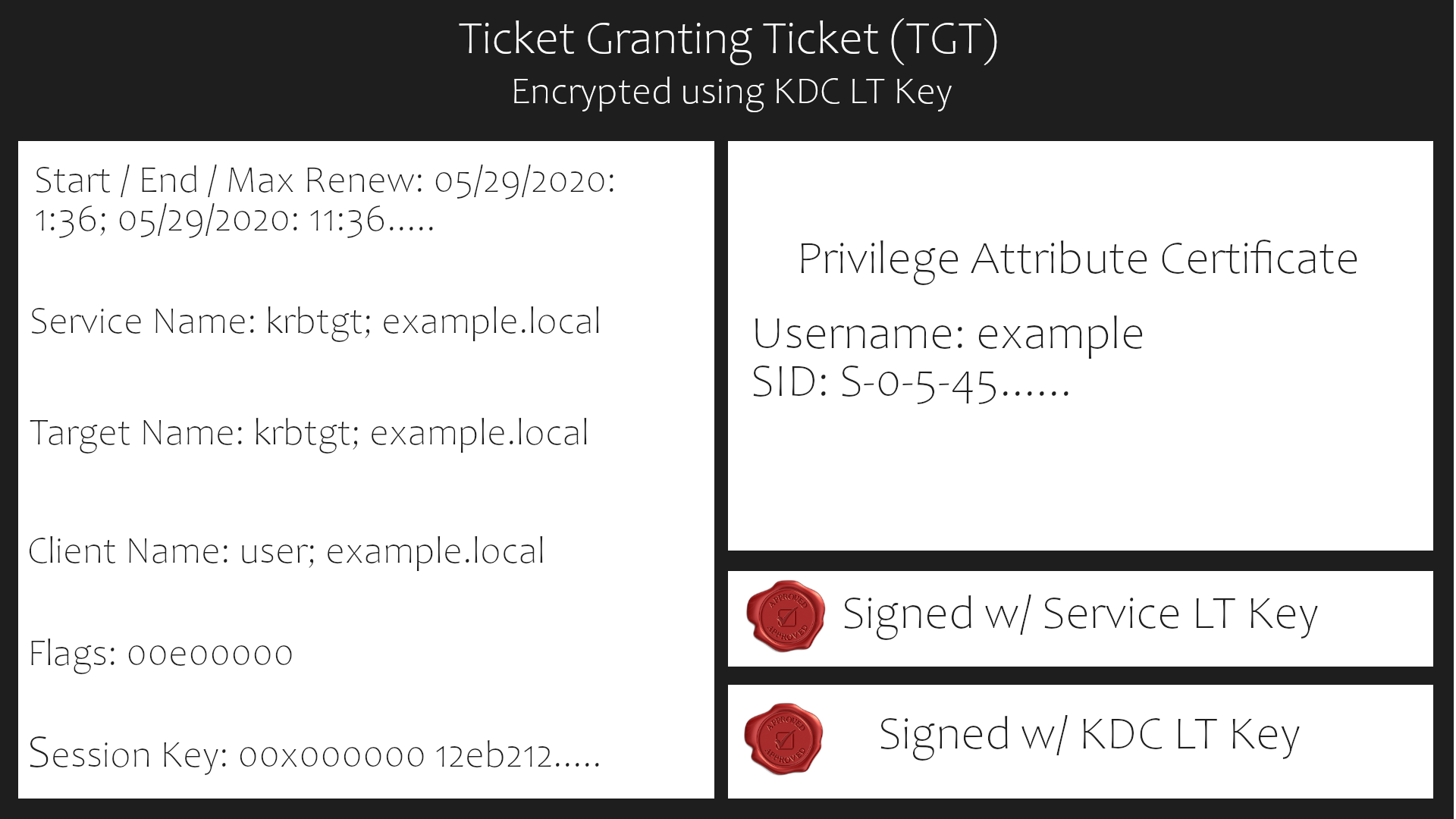
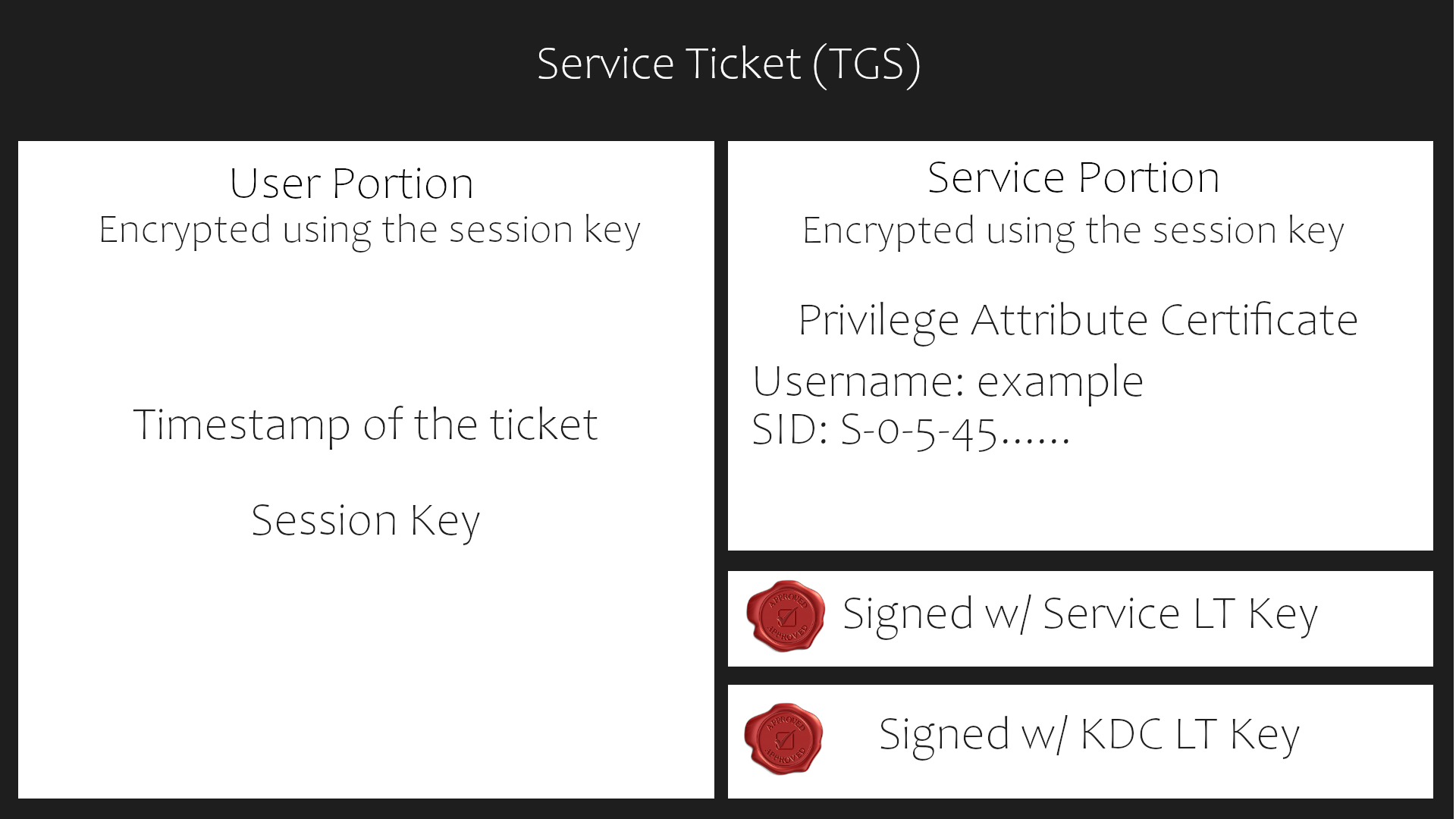
So what does a ticket contain? Basically tickets contains a client's Id, service ID, session keys, timestamp, time to live and other informations which are encrypted using a server's secret key.
High level overview for users to gain access to a service
First the user sends an unencrypted message to the authentication server(AS) saying HEY! i would like to access some service
Second the authentication server(AS) validates that the message is coming from a known user and generates a TGT(Ticket Granting Ticket)which is sent back to the user encrypted with the user's secret key.(shown in second arrow from athentication server to the user)
Third the user decrypts the message with their secret key and creates new messages then sends the message along with their TGT to the Ticket Granting Server
Now the Ticket Granting Server decrypts the TGT, performs some validation and generates a service ticket(ST) which is sent to the user along with new message
Again the user decrypts the message and creates an authenticator message and sends the message and the service ticket to the service he wants to access
At last the service does its own validation and sends the user a final authenticator message
Above steps in short
AS-REQ(AUTHENTICATION SERVER-REQUEST): The client requests TGT from the authentication server. When the client requests for TGT they will send an encrypted timestamp along with the request. The timestamp is encrypted with the user's password.
AS-REP: The Authentication server verifies the client and sends back an encrypted TGT, this TGT is encrypted using the password hash of krbtgt account.(Golden ticket comes into play at this step if we get password hash for the krbtgt account using for example secretsdump.py from impacket we can forge ticket for any account or service we want we are gods then)
TGS-REQ: The client sends the encrypted TGT along with the SPN(Service Principl Name)to the Ticket Granting Server, SPN means which service the client wants to access alex\MYSQLcomputer$@domain.local.
TGS-REP: The TGS verifies the TGT of the user and sends a ST for the requested service. This ST is encrypted with the NTLM hash of the service.Here the TGS doesn't verify if the client has access to the requested service.(Kerberoasting attack)
AP-REQ(AUTHENTICATION PROTOCAL-REQUEST)the client sends request to the service requesting for access by sending that ST ticket
AP-REP: The service verifies whether the user is authorized or not by trying to decrypt that ST and grants access if possible.
TGT contents
ST contents
User Enumeration
nmap automated query everything from ldap ports(output may be tedious)
AsrepRoasting
After enumeration of valid users we try to enumerate for asreprostable accounts.asreprostable accounts are the accounts which has Does not require Pre-Authentication option set, which means when the client first sends request to Authentication server asking for TGT it doesn't need to send an encrypted timestamp as normally it should as told in above AS-REQ step. This attack is known as ASREPROASTING for this we use tool from impacket called GetNPUsers.py
To get TGT for a valid user(Only if donot require pre authentication is set):
OR
Cewl for generating passwords for password spraying
Spraying Password
we can also try spraying a single password or list of passwords against the usernames we found using crackmapexec.
Now lets assume we have compromised a user and we have his password we can query for other available users in the domain using GetADUsers.py which will prompt for the password
Now lets suppose you are inside a domain now we can use PowerView.ps1 or Bloodhound to enumerate further the domain. We can also use bloodhound.py
After landing inside the network
Which users are currently logged on in this machine
net logonsextract all domain users
extract all Domain Admins
Find logged in users of high value groups(Domain Admins group)
Find service accounts based on SPN
Kerberoasting
We just need regular service account credentials to perform this attack.Kerberoasting is a post exploitation attack against service accounts where we harvest Service Tickets for the service accounts using SPN(Service Principle Name) for eg: WWW/WEB-SERVER01@htb.local this SPN means web service is running on htb.local computer as WEB-SERVER01 service account..Since Service Tickets are encrypted with NTLM hash of the service account which can be cracked offline. Simply kunai pani regular domain user to credentials payesakepachi aba tyo user ley domain ma run vako kunai pani service ko lagi ST magxa TGS server sanga ra tyo ST service account ko NTLM hash ley tyo encrypt vako hunxa tesaile yo ntlm hash extract garera tyo service account ko password crack hanna paiyo
Using powershell and Invoke-Kerberoast powershell script after doing
. .\Invoke-Kerberoast.ps1
Or save the hash in a file
Manual kerberoasting method (1)
(2)
(3)
Ok so now we are inside the domain but as a domain user not as any privilege user so we use windows privilege escalation techniques,find misconfigurations,use winpeas to become a privilege user or some local admin.Lets suppose we are now a local administrator.
Use ldapdomaindump after compromising a single user to extract computer,groups,users and other information in html format which can be viewed nicely from browser
Stealing hashes
mimikatz:
powershell mimikatz:
GPP credentials(Privilege escalation / Lateral movement)
GPP was introduced in windows server 2008 This technique may not work on modern domain controllers. It may work up to windows server 2008 and 2012. GPP stands for Group Policy Preferences where Preferences means settings and GPP means settings and configurations for group of Domain joined computers on the network these settings includes setting local user password, mapping share drives, adding local users to groups, adding local users to printer,exchange or other services and so on, most of these actions require some form of authentication. In a Domain controller there is a folder under C:\Windows\SYSVOL which is also a share to which all authenticated users has read access to. This share contains all the Group policy objects are stored in \\SYSVOL<DOMAIN>\Policies\ folder and the objects are basically folders with structure like this {31B2F340-016D-11D2-945F-00C04FB984F9}. Inside these folders under MACHINES\Preferences\Groups folder we can find Groups.xml file which contains username and cpassword(encrypted password).
The password is encrypted with 32 bit AES key and microsoft had released the key for some reason in 2012, acticle:- https://docs.microsoft.com/en-us/openspecs/windows_protocols/ms-gppref/2c15cbf0-f086-4c74-8b70-1f2fa45dd4be?redirectedfrom=MSDN So we can easily crack the password for the user using gpp-decrypt tool in linux as follows.
Abusing Active Directory ACLs
GenericAll - This permission allows attackers full rights to the object(create users, add users to a group, reset user's password, etc) Example of adding a new user to Exchange Windows Permissions group(Object) where our compromised user has GenericAll privilege.
WriteDacl - DACL is an internal list attached to every object in active directory,this list specifies which users and groups can access the object and what kind of operations can they perform on the object, for example a file access can have read access assigned but a printer cannot have read access assigned since we cannot read a printer right? By default the owner of an object has permission to modify its DACL. Suppose our owned user or group has WriteDacl privilege on a domain htb.local, this means we can modify DACL (Discretionary Access Control List) of htb.local domain which means we can grant ourselves any privilege on the object of that domain, here we want to grant our user DCsync privilege or in simple terms we are assigning our user Active Directory Domain Replication Rights. What is DCsync in brief? DCSync is a late stage kill chain attack this means an attacker has hold of a user who has Active Directory Domain replication rights, domain replication is the method of updating objects from one DC to another DC and during this process the DC returns replication data to the requester including password hashes.
![[dcsync.png]]
Attacking Steps:
Here we are just creating PS credential object of user alex supposing we have already created a AD user named alex through GenericAll privilege or any methods. We are creating PS credential object of alex because who has time to add alex to winrm group and again login as alex via evil-winrm or adding alex to RDP users, opening RDP port if not opened and all bullshit.
Now we will use PowerView's Add-DomainObjectAcl function to provide DCSync rights to our user alex
After this we can use secretsdump.py from impacket to dump all hashes
After getting Administrator hash we can just utilize pass the hash attack using evil-winrm, psexec or other tools
SeBackup and SeRestore privilege
If both SeBackupPrivilege and SeRestorePrivilege are enabled on a user we compromised in an Active Directory environment, we are able to take the copy of NTDS.dit file and obtain password hashes of every user on the domain. To abuse this we download two dll files SeBackupPrivilegeCmdLets.dll and SeBackupPrivilegeUtils.dll from https://github.com/giuliano108/SeBackupPrivilege these two dlls can be found on /SeBackupPrivilegeCmdLets/bin/Debug folder once we clone the repository. We need to upload these two dll files in a writable directory in victim host lets suppose inside C:\temp folder. Now inside C:\temp folder run both dlls.
Since the NTDS.dit file is constantly in use with the domain controller we cannot copy it and may get error saying this file is being used by another process in order to get around this problem we can use diskshadow which is a builtin tool in windows to create copy of drive that is currently in use.We can pass actual file as arguments to diskshadow as .dsh files. First we create a .dsh file(Distributed Shell File) saving the following as alex.dsh in our attacking box. Here we are instructing the diskshadow to create copy of c drive into z drive with alex as its alias.
alex.dsh file
Now we convert this alex.dsh file's encoding and spacing using unix2dos.
Upload alex.dsh into victim host inside same wriatble directory as previous dll files and run diskshadow as follows.
After running this we will have a full copy of c drive into z drive now we can use the Copy-FileSeBackupPrivilege function from previous dlls and copy the NTDS.dit file from z drive into our temp folder as below
After this we also need to save the system registry hive as follows
Download both ntds.dit and system.bkp into our attacking machine and now we can extract all the hashes using secretsdump.py as follows which we can leverage using pass the hash attack.
SeRestore Privilege
We can use this privilege to take control over services in the registry and modify the service path and when the service is started it will execute as system. For this we can use SeRestoreAbuse tool by xct https://github.com/xct/SeRestoreAbuse. We have to re login for this in order to take affect.
SeBackup Privilege
We may be able to change the ACLs on an object using this privilege to abuse this privilege we can use https://raw.githubusercontent.com/Hackplayers/PsCabesha-tools/master/Privesc/Acl-FullControl.ps1
Now we can take control over the Administrator folder.
Pass the hash(Lateral Movement)
After getting nt authority\SYSTEM on a client computer we can load mimikatz to dump hashes and use the NTLM hash of dumped users to authenticate against other computers or dc.
Suppose we find ntlm hash of user james now we can use crackmapexec to spray the hash to other computers and use psexec to get access to that particular pc.
Over Pass the hash(Lateral Movement)
After getting nt authority\system on a client computer(RDP access) we can extract the ntlm hashes using mimikatz as above but if ntlm authentication is not supported or disabled we can leverage this technique to move laterally to other computers.
Here suppose we got the ntlm hash of james(A high value user who has session on another computer example dc01 the domain controller) using mimikatz but ntlm authentication is disabled so we cannot use the ntlm hash to authenticate to other computers.
We need RDP access on a client computer after getting nt authority\SYSTEM we load mimikatz then do the following to first run powershell process as high value user whose ntlm hash we captured
overpass the hash uses logon type 9 which means running whoami still shows as default username or user who started the process but we can access the remote resource like the domain controller or other machines simply by doing
winrs -r:dcorp-dc cmd
Another technique using over pass the hash
At this point, we have a new PowerShell session that allows us to execute commands as james(high-value-user who has session on dc01 computer)
From the powershell prompt we can use net use command to generate a TGT
After this we will have valid TGT and TGS, now transfer psexec.exe to that computer and from the same powershell session launch psexec as follows
We will be logged into dc01 computer which is essentially the domain controller in this case.
Golden Ticket(Persistance technique)
This attack is usually a final kill chain attack which involves forging a valid TGT as any user using the NTLM hash of krbtgt account. After a user has sent AS-REQ during initial login the authentication server validates that the user who is requesting for TGT exists on the database and if it does sends an encrypted TGT(AS-REP step), this TGT is encrypted using the password hash of krbtgt account. This krbtgt NTLM hash can be obtained from the lsass process, from NTDS.dit file, using mimikatz and performing lsadump::dcsync or usually from impacket example's secretsdump.py module however every technique requires the attacker to have domain admin privilege. After getting the ntlm hash for krbtgt account we can use ticketer.py from impacket or mimikatz in case of windows to forge valid TGT for any user or service on the entire domain. To get the domain's SID we can use Get-DomainSID function of powerview.
In linux after getting SID of dc and ntlm of krbtgt using secretsdump.py
In windows after executing mimikatz.exe
Silver Ticket
Looking into step 6 of above kerberos authentication step, when the user presents the ST to the service, the only validation done at the service level on the authenticity of the ST is if it can decrypt the ST presented by the user. If we somehow grab the NTLM hash of the service or if that service is running in contex of comprmoised user account we can just get hash for that service using the password of that compromised user after this we can forge ST(make our own ST) pretending to be administrator or anyone to that service. For example we have compromised a user on behalf of whom MSSQL service is running as by using password of that compromised user we can simply grab the ntlm hash for MSSQL service and forge our own ST for MSSQL service pretending to be domain admin, administrator, or any privileged user to MSSQL service. If this MSSQL service is running on domain controller dc.htb.local, pretending to be Administrator to this service results into being Administrator itself on entire domain.
In windows after compromising user account who is running a service
Step 1(Getting service hash for that service)
Step 2(Creating a forged ST)
In windows this is it now we will be Administrator for htb.local domain but for only MSSQL service,here this MSSQL service is running on dc.htb.local it means we are Administrator on entire domain.
In linux after getting the nthash of service account(need to figure out how to generate nthash using password of user on behalf of whom that service is running as)
Note: If the service can delegate as another service suppose MSSQLsvc is allowed to delegate as WWW service we can generate silver ticket for MSSQLsvc providing spn as WWW/htb.local which gives us access as Administrator on web service
Attacking gMSA(group Managed Service accounts)
First, what are MSA? These are called Managed service accounts and they eliminate the need for administrators to manually set password for service accounts, they cycle the password regularly as well as support simplified SPN management that's why these are known as Managed service accounts. There are two types of MSA they are sMSA(standalone Managed Service Accounts)which was released by microsoft in windows server 2008 R2 and windows 7 to provide automatic password management,simplified SPN,etc another is gMSA(group Managed Service Accounts) as the name suggests group meaning these services run on contex of groups itself rather than standalone and just like sMSA they provide automatic password update, password cycling, supports simplified SPN,etc however they fail to protect the credentials. The following are the some attributes specific to gMSA
msDS-GroupMSAMembership (PrincipalsAllowedToRetrieveManagedPassword) – stores the security principals that can access the gMSA password.
msDS-ManagedPassword – This attribute contains a BLOB with password information for group-managed service accounts.
msDS-ManagedPasswordId – This constructed attribute contains the key identifier for a group MSA’s current managed password data.
msDS-ManagedPasswordInterval – This attribute retrieves the number of days before a managed password gets automatically changed for a group MSA
Now, simply an attacker who has already compromised a regular domain user can use
To find out which groups can retrive the password or hash for this service and if the compromised user is part of that group we can extract the password or the service hash. Simply during enumeration using bloodhound or ldapsearch like shown here if we find something like
and if this service is allowed to delegate to other privileged services or is a pivot point for high value targets we can try using regular domain user credentials to just try dumping the password or hash for that service.(if our compromised domain user belongs to one of the groups that manages this service we can extract else not)
https://github.com/micahvandeusen/gMSADumper
Here in inteligence machine we got credentials for Ted.Graves and since during enumeration using ldapsearch we found a service named svc_int which was a gMSA we tried using credentials of Ted.Graves to dump the credentials for that service and indeed Ted.Graves was part of itsupport group and svc_int service was run on behalf of this group too.
MS14-068(Windows Server 2008 R2)
The MS14-068 flaw in Kerberos allows a regular authenticated domain account to elevate permissions to compromise an entire domain.The attacker just needs to have standard domain account for this attack.The vulnerability exists when the Microsoft Kerberos KDC implementations fail to properly validate signatures, which can allow for certain aspects of a Kerberos service ticket to be forged. Manual exploitation of this vulnerability can be found here https://wizard32.net/blog/knock-and-pass-kerberos-exploitation.html and more deeper manual exploitation process can be https://adsecurity.org/?p=676. Mantis from hackthebox was related to this attack. However goldenPac.py from impacket allows automatic exploitation of this vulnerability.
Sync the local time with the time of Domain controller
Exploitation(Example from Mantis box hackthebox, use FQDN as shown example.internal.local at the end)
CVE-2020-1472 Zerologon
CVE 2021-42278 and CVE 2021-42287(samAccountName Spoofing and Domain Controller Impersonation) This works upto any AD environment and latest windows server upto 2019
For this exploit we just need a regular domain account doesn't have to have any privilege. Combining CVE 2021-42278 and CVE 2021-42287 it is possible for a regular domain user to impersonate a domain admin. CVE 2021-42278 is an Invalid Computer Account Name issue, since computer accounts in AD always ends with $ but this is not enforced properly and an attacker can create a computer account name same as the domain controller name but without $. Suppose the DC name is dc01$ here a regular user can just rename his computer to dc01 without the $ because of course we cannot have two computers with the same name. Now CVE-2021-42287 (KDC confusion), during the kerberose authentication process a TGT is sent to the client and this TGT is used to request access tokens from TGS(Ticket Granting Server) for specific resource/systemn in the domain now when a request for ST is sent by client and if it is not foundTGS-REQ step, the TGS will lookup the requested ticket appended with $. Combining these two issue the exploitation steps is as follows
A new computer account is added to the domain.
The created computer account is renamed to match the name of an existing domain controller (without the trailing ‘$’)
A Kerberos TGT is requested using the updated computer account name.
The created computer account name is once again renamed to its original (or any) value.
A Kerberos Service Ticket is requested using the S4U2self extension.
Now this ST can be used to used to access any service on the domain controller
Last updated